He worries about his next doctor’s appointment, a brief checkup.
He worries about his relationship with his partner of seven years. And he worries a lot about his work as an IT manager at Simpson & Jones Law.
One of his worst fears? Disappointing people who count on him.
What does he do?
The answer: it depends. If his organization enjoys a comprehensive, automated security system like the kind offered by Cisco Meraki, he can safely return to bed. If, though, he’s relying on a tech stack piled high with assorted point solutions—or even less—he’s fighting an uphill battle against a far more prepared foe.
When the Worst-Case Scenario Hits
If you work in the IT field, you’ve had some variation of this dream before.
Your boss calls you—maybe in the middle of the night—and tells you that something’s gone terribly,
terribly wrong.
For Ted, it’s always a call from his boss, Yvonne.
“Someone must have gotten into the client database,” she tells him.
“What? What happened?” he asks frantically.
“I don’t know, Ted. But you need to fix it.”
Cue the panic.

Neutralizing the Threat with Meraki
In reality, Ted took care to make sure every branch had measures in place to stop attacks like these. So, when his boss recently called him at work about a threat, Cisco Meraki had Ted—and Simpson & Jones—covered.
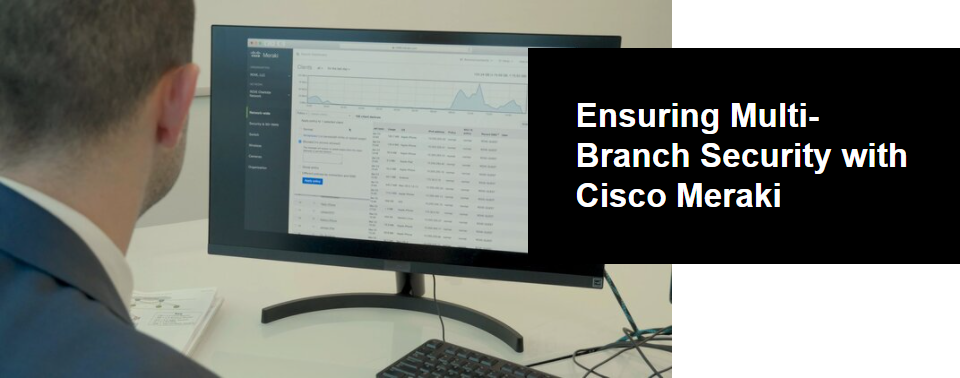
As soon as he caught wind of the attack, Ted opened his Meraki dashboard, which he uses to manage and secure the organization’s network infrastructure. He navigated to the map view and began to sort through the organization’s Charleston, Augusta and Greenville branches.
The Meraki dashboard pinpointed the threat to a computer in the Augusta office. Meraki allowed him to immediately quarantine the device, shutting it down and effectively preventing the infection from spreading further into the network.
The Non-Meraki Nightmare
In Ted’s nightmares, he doesn’t have Meraki, and therefore doesn’t have clear visibility into every branch’s network activity. Instead, he finds himself stuck calling different office branches, talking to employees and taking notes, trying to piece together what happened. His days become consumed with following dead ends, scrubbing through security footage from each branch and attempting to control the damage.
In those recurring nightmares, Ted usually finds himself with one option left. He calls his boss.
“We have to shut the whole network down,” he tells her.
“For how long?”
Without Meraki, he doesn’t have an answer.

Ted Locates the Perpetrator
When the recent real-life attempt occurred, Ted was able to put together the pieces easily.
Luckily, he had made sure there were Meraki security cameras throughout each branch office. He checked out the motion-detection records on the Meraki dashboard, where security footage is captured and analyzed.
He discovered that three motion alerts occurred on the night of the breach—two at the stairwell, one in the server room. The timestamps corresponded to the timing of the breach, and the images clearly showed the perpetrator’s face—a former employee, recently hired by an unscrupulous competitor.
Ted immediately reported the news to Yvonne, and the evidence was passed to law enforcement.
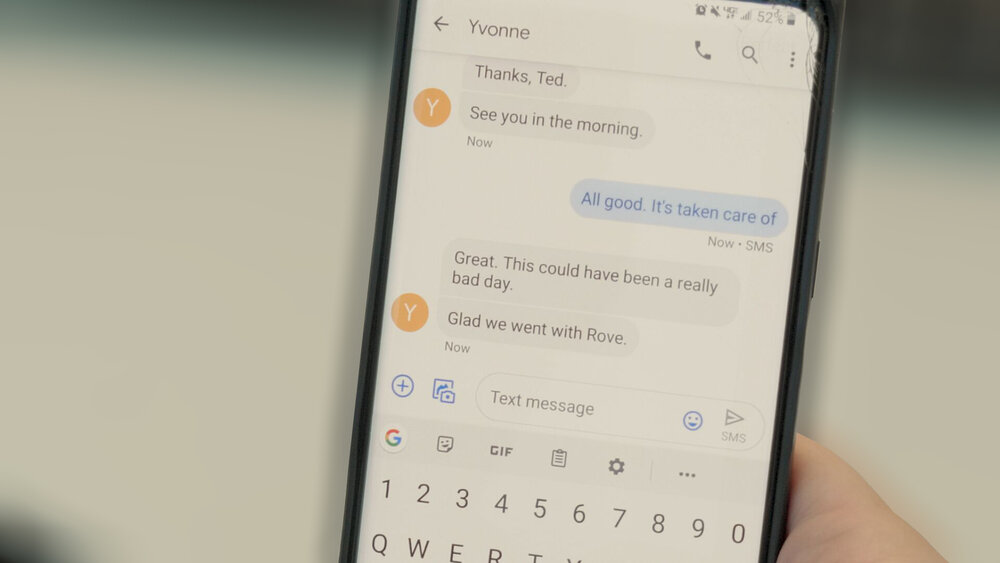
Sleep Soundly with Meraki
If you, like Ted, lose sleep due to fears of an increasingly likely cyberattack, ROVE is available as a true consulting partner and IT marketplace. Through our consulting-led approach, we help your organization navigate the complexity of modern security, assisting you in discovering the best tech beneath the hype.
We also offer a marketplace specially designed to ensure IT consistency across your multiple branches. You can login and view all IT equipment at each branch to avoid redundancies, blind spots and security holes.
Want to see a similar cyberattack scenario in action? Watch our video that follows IT manager Ted through the steps of a security breach, with and without Meraki.